The Role of MD5 Hash Function in Encryption
Introduction: Data security is paramount in today's digital age, where cyber threats continue to proliferate. Companies and individuals rely on encryption techniques to safeguard their data from unauthorized access and theft. The MD5 hash function plays a significant role in encryption operations, and in this article, we'll explore its role and importance in data security.
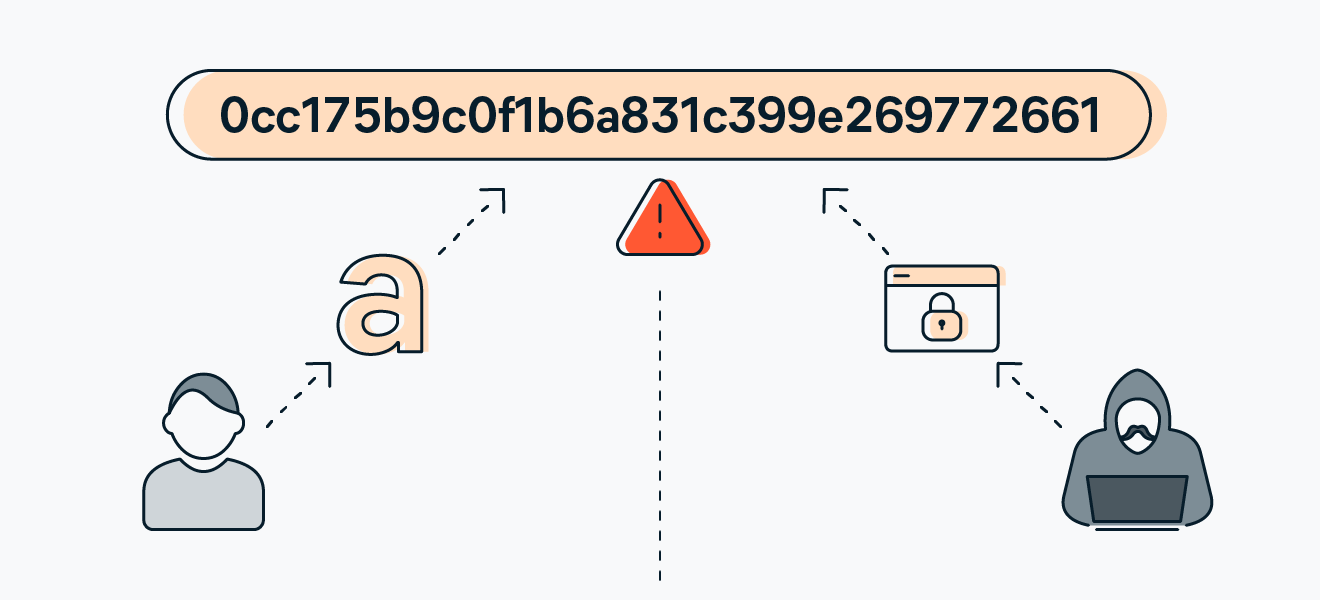
Understanding MD5: MD5 (Message Digest Algorithm 5) is one of the most widely used cryptographic hash functions. This algorithm generates a unique set of digital characters to represent a specific piece of data, and this representation is used to verify data integrity and detect any unauthorized changes.
Importance of Encryption for Data Security: Encryption operations are essential for protecting data from unauthorized access. Through encryption, intruders are prevented from decrypting data and gaining access easily. Here are some key importance of encryption in data security:
- Privacy Protection: Encryption safeguards sensitive data such as personal and financial information from unauthorized viewing.
- Identity Verification: Encryption allows for verifying the identity of the user and the integrity of the exchanged data.
- Tamper Prevention: Encryption prevents data tampering by confirming its integrity and ensuring it hasn't been altered.
The Role of MD5 Hash Function in Encryption: The role of the MD5 hash function lies in generating a unique set of digital characters known as a "hash" or "digest" for the data. While MD5 is not a perfect substitute for secure encryption due to its susceptibility to collision attacks, it is still widely used in many security applications and identity management systems.
Conclusion: Technologies operating in the field of encryption, including the MD5 hash function, play a crucial role in protecting sensitive data in the digital world. By understanding the role and importance of the MD5 hash function, companies and individuals can enhance the security of their data and guard against potential cyber threats.